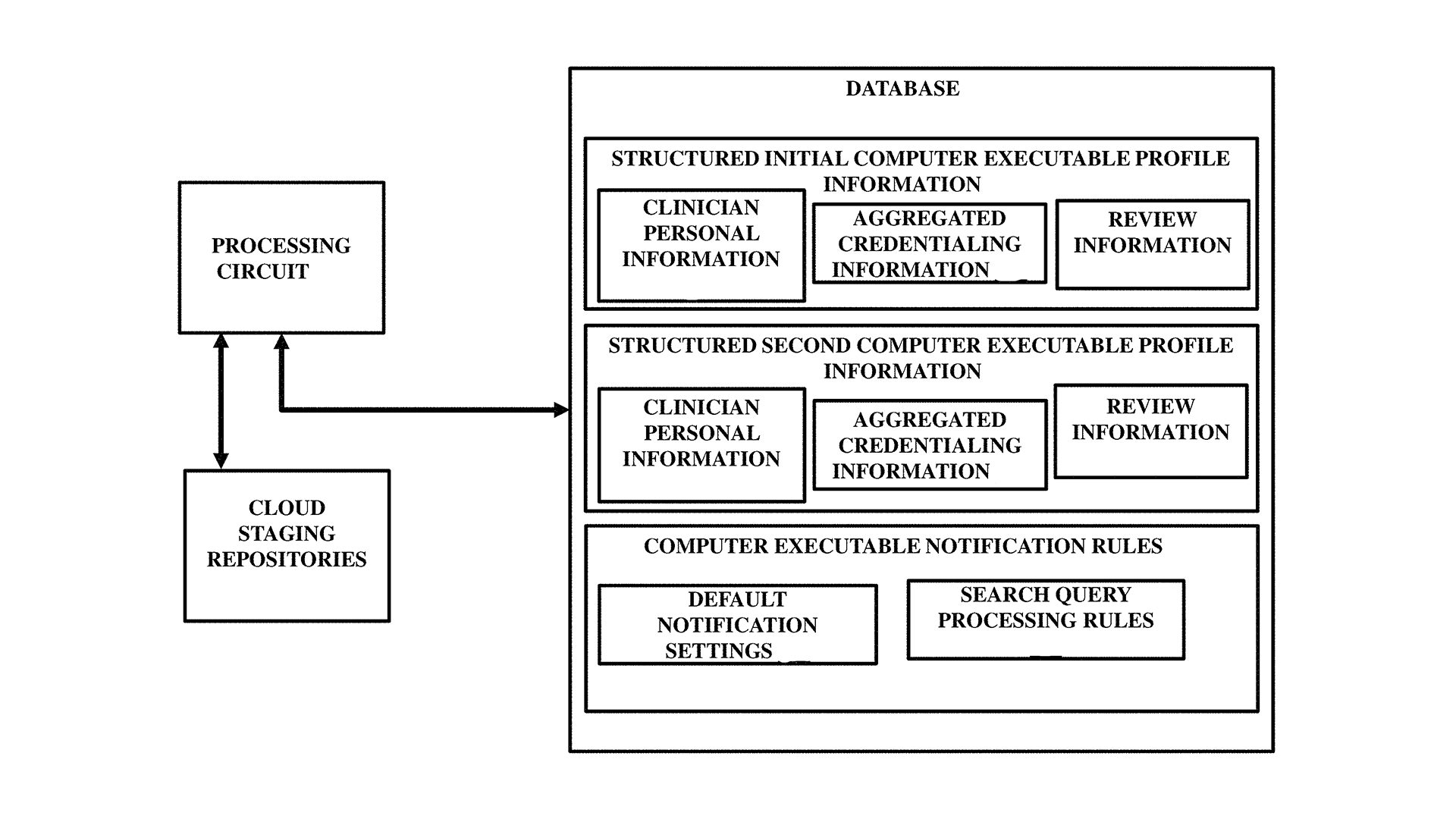
Efficient Method for Tracking Changes in User Profiles Over Time
From social networking sites to professional platforms, profiles act as a digital representation of individuals and entities, which is why web-based profiles are considered ubiquitous.

From social networking sites to professional platforms, profiles act as a digital representation of individuals and entities, which is why web-based profiles are considered ubiquitous.

In the rapidly evolving digital era, people increasingly turn to online crowdsourced networks to find answers and solutions to a wide array of queries and challenges.

The integration of blockchain presents an innovative solution to longstanding problems in the medical data management sector, particularly in the context of natural language processing in healthcare.
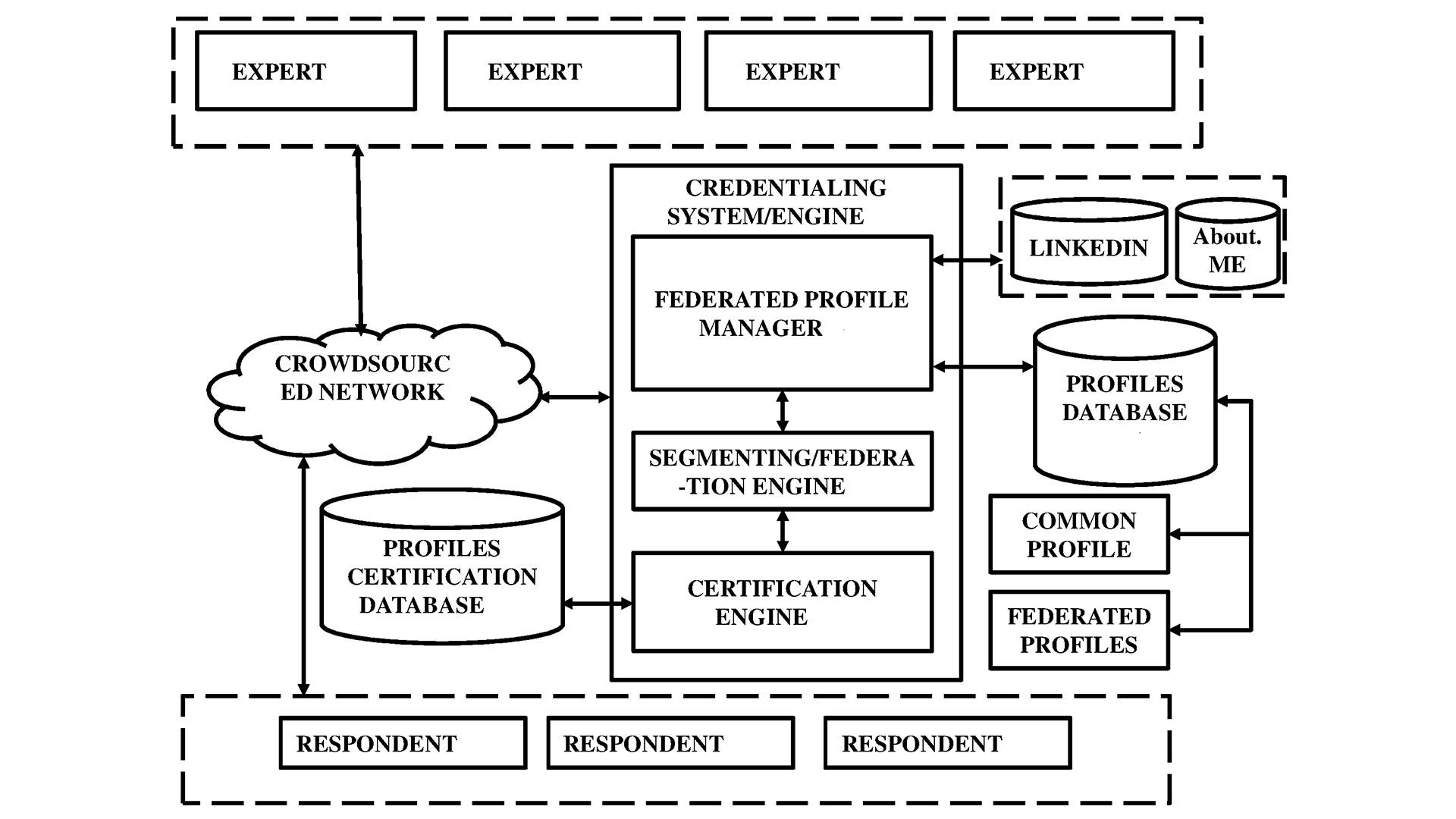
This inventive technology described in this content addresses a critical problem faced by organizations when it comes to evaluating electronic documents, particularly in the context of selecting valuable ideas for financial aid or rewards.
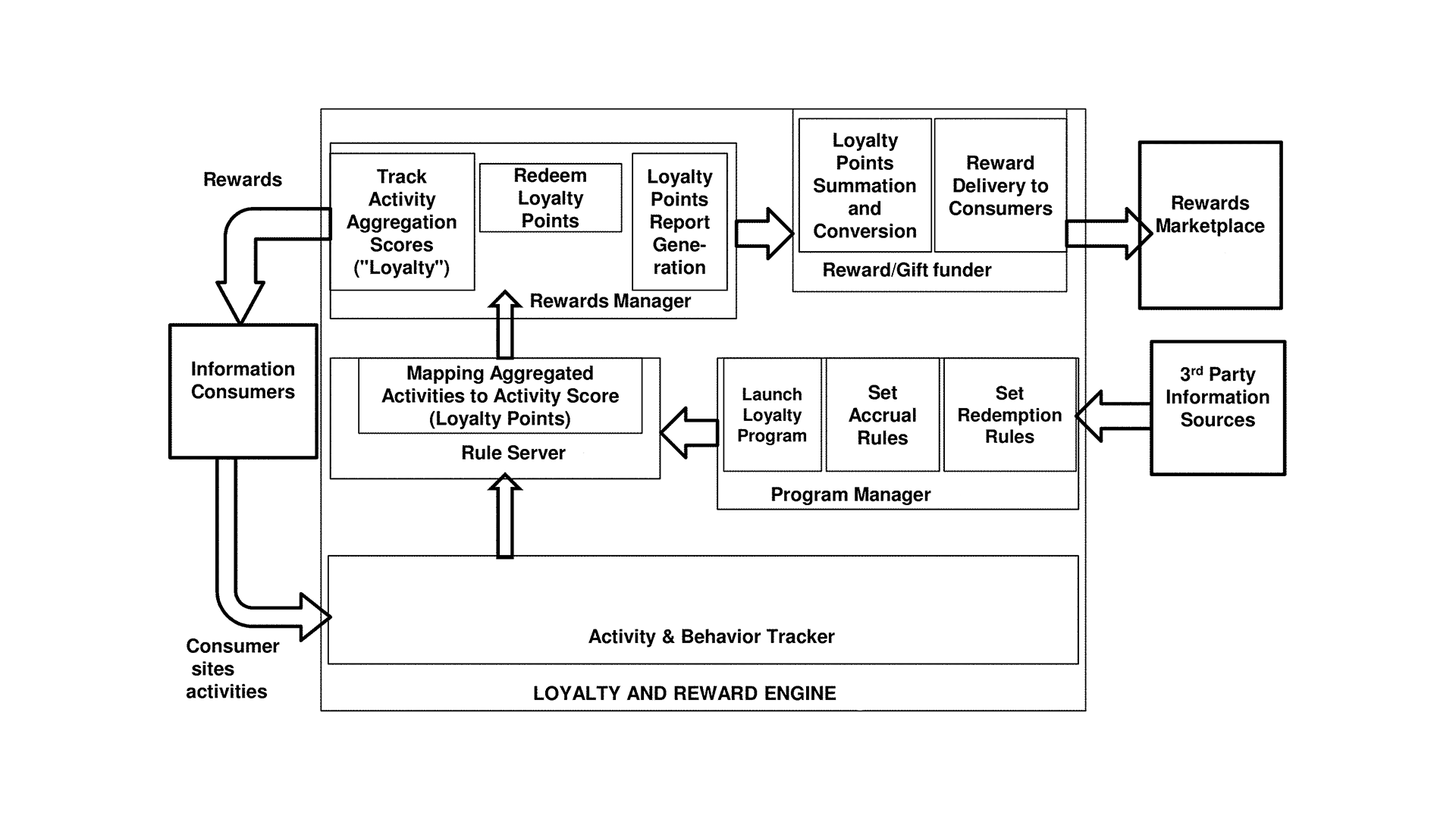
Electronic Medical Records (EMRs) have revolutionized modern healthcare, providing a streamlined mechanism to capture, maintain, and analyze patient data electronically.

The evolving framework of health care informatics faces multiple technological hurdles. Predominantly, medical institutions, encompassing tertiary care hospitals, geriatric care facilities, and ambulatory clinics, curate an expansive databank of patient-centric records.
This technology establishes a secure and trust-based system for exchanging crowdsourcing innovation in an ecosystem.
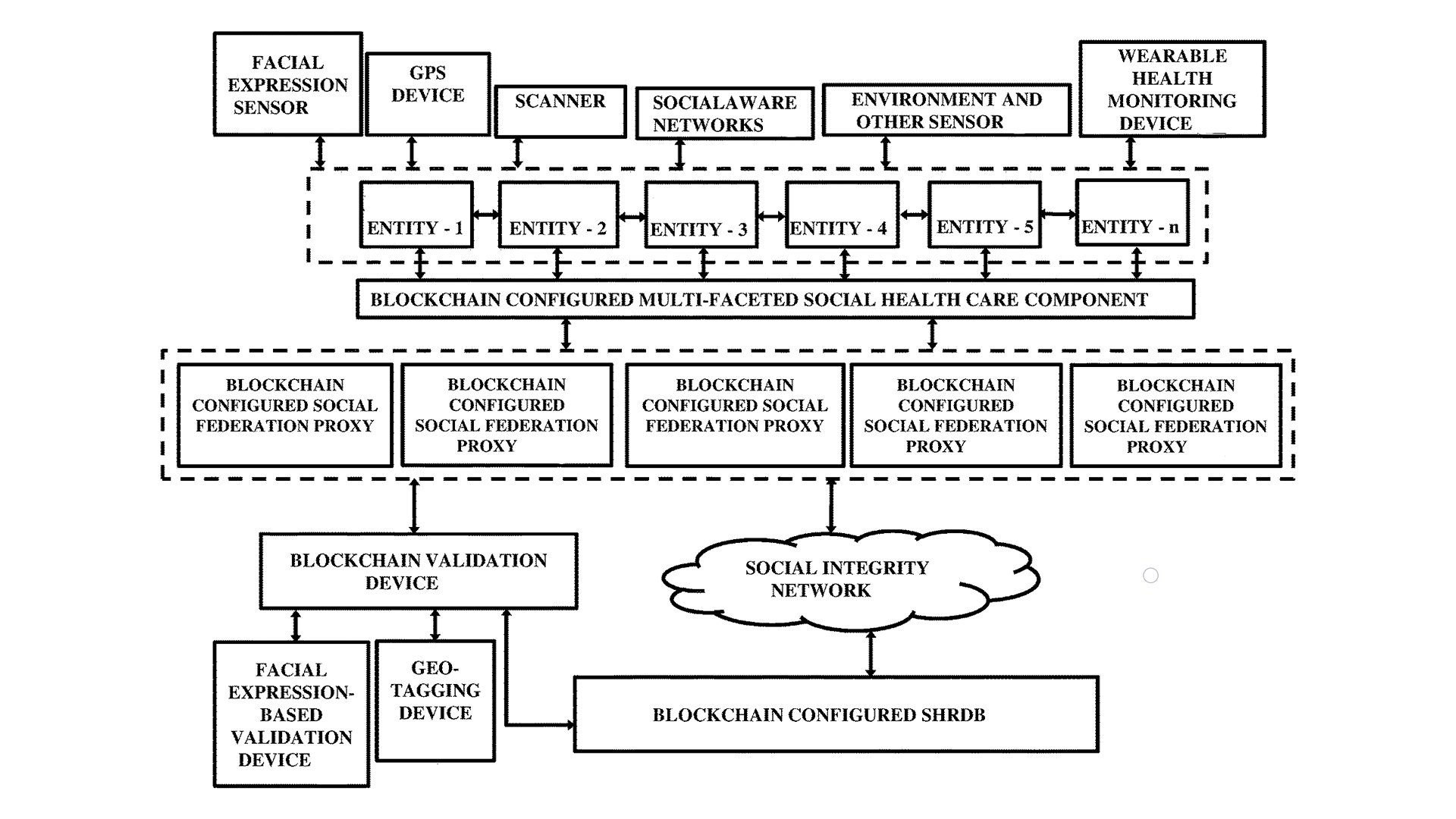
In healthcare organizations, the maintenance and accessibility of patient data stand as an essential element for effective medical care.
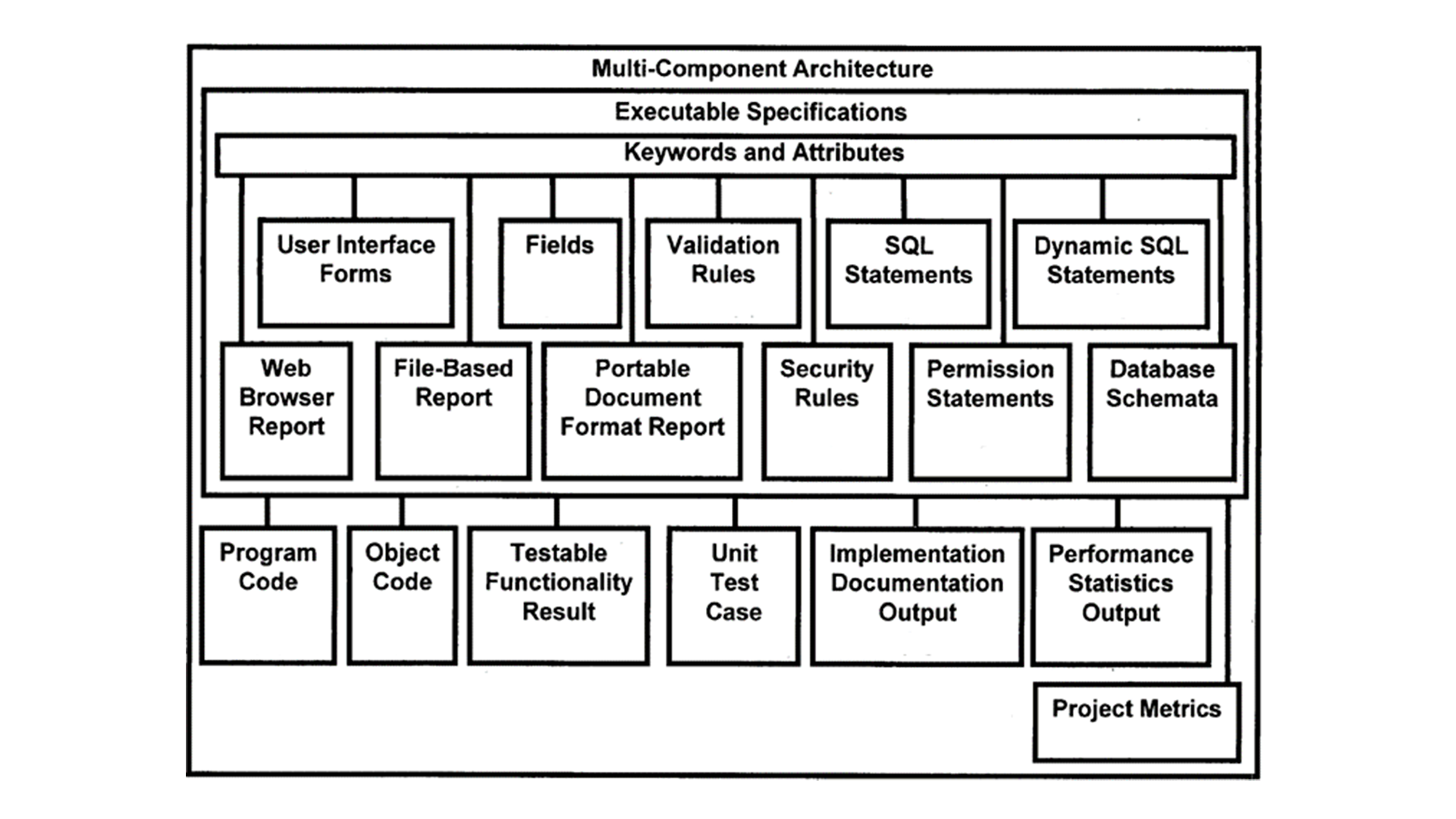
In the progression of computer software applications, the primary objective has always been enhancing the productivity of entities, ranging from individual professionals to vast enterprises.

When a service is rendered by a service provider to a beneficiary, and the payment claim is directed to a third entity, the critical quandary arises on how one can reliably validate that the service was provided on a genuine ground.